MalwareTech Challenge - strings1.exe
I have been teaching myself to reverse engineer binary programs so that I can use these skills to reverse engineer malware. I have been learning assembly code, and playing with new tools such as ghidra and radare2/cutter.
I found that @MalwareTech had some great binary analysis challenges on his blog and decided to check them out.
This write up covers the first challenge strings1.exe: ‘https://www.malwaretech.com/strings1’
Lets open this binary in cutter and analyze it with radare2. Once open lets navigate to the entry fucntion:
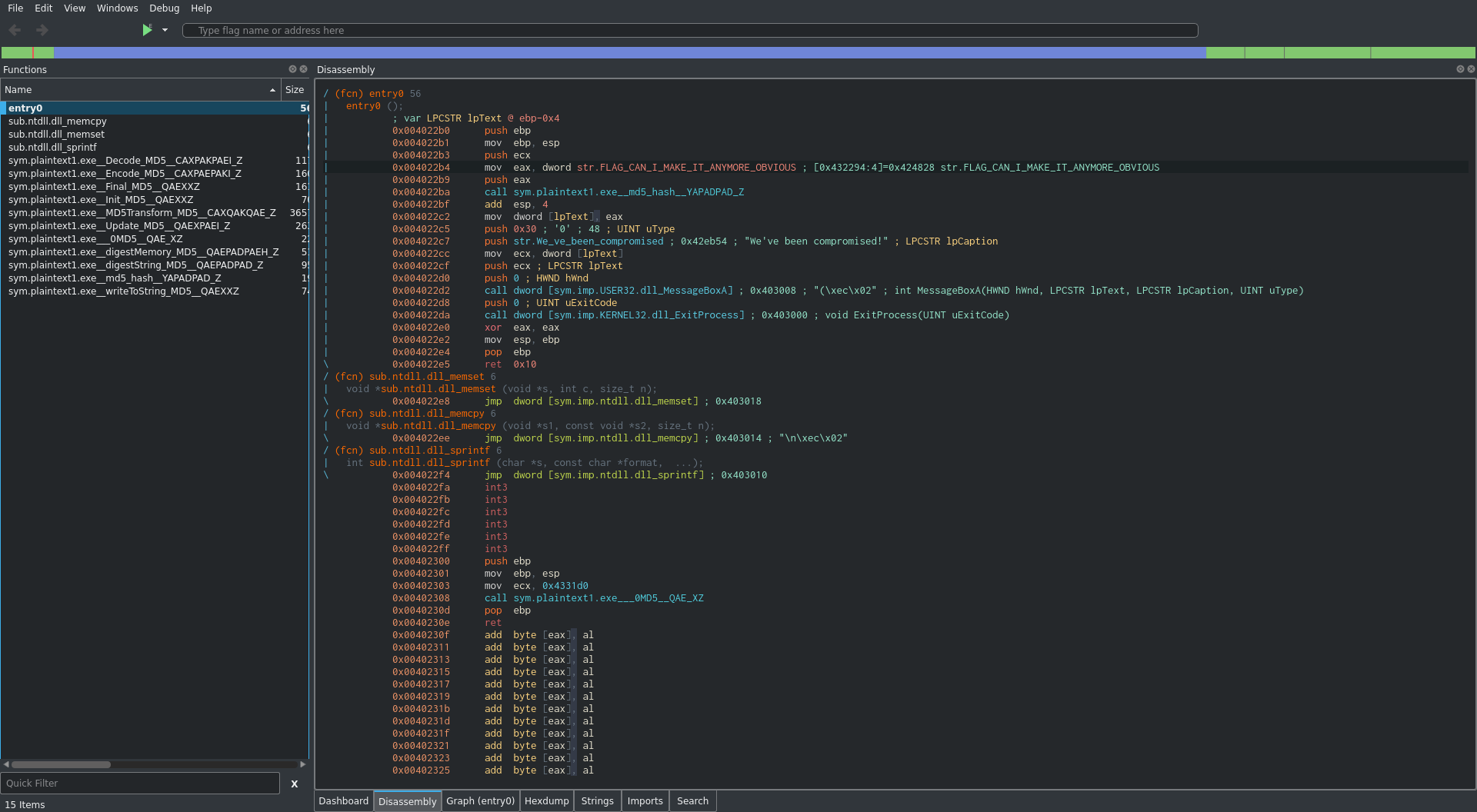
Right away it looks like we have the flag, but lets look at this code:
entry0 ();
; var LPCSTR lpText @ ebp-0x4
push ebp
mov ebp, esp
push ecx
mov eax, dword str.FLAG_CAN_I_MAKE_IT_ANYMORE_OBVIOUS ; [0x432294:4]=0x424828 str.FLAG_CAN_I_MAKE_IT_ANYMORE_OBVIOUS
push eax
call sym.plaintext1.exe__md5_hash__YAPADPAD_Z
add esp, 4 ; clear the stack
mov dword [lpText], eax
push 0x30 ; '0' ; 48 ; UINT uType
push str.We_ve_been_compromised ; 0x42eb54 ; "We've been compromised!" ; LPCSTR lpCaption
mov ecx, dword [lpText]
push ecx ; LPCSTR lpText
push 0 ; HWND hWnd
call dword [sym.imp.USER32.dll_MessageBoxA] ; 0x403008 ; "(\xec\x02" ; int MessageBoxA(HWND hWnd, LPCSTR lpText, LPCSTR lpCaption, UINT uType)
push 0 ; UINT uExitCode
call dword [sym.imp.KERNEL32.dll_ExitProcess] ; 0x403000 ; void ExitProcess(UINT uExitCode)
xor eax, eax
mov esp, ebp
pop ebp
ret 0x10
Looking at the assembly it looks like we are accepting a value to this function: lpText. This is likely the variable that we will enter when asked for the flag. After that the stack is initialized and a string containing the correct flag is pushed to the stack from .rdata 0x424828. Lets look at a hexdump of that offset:
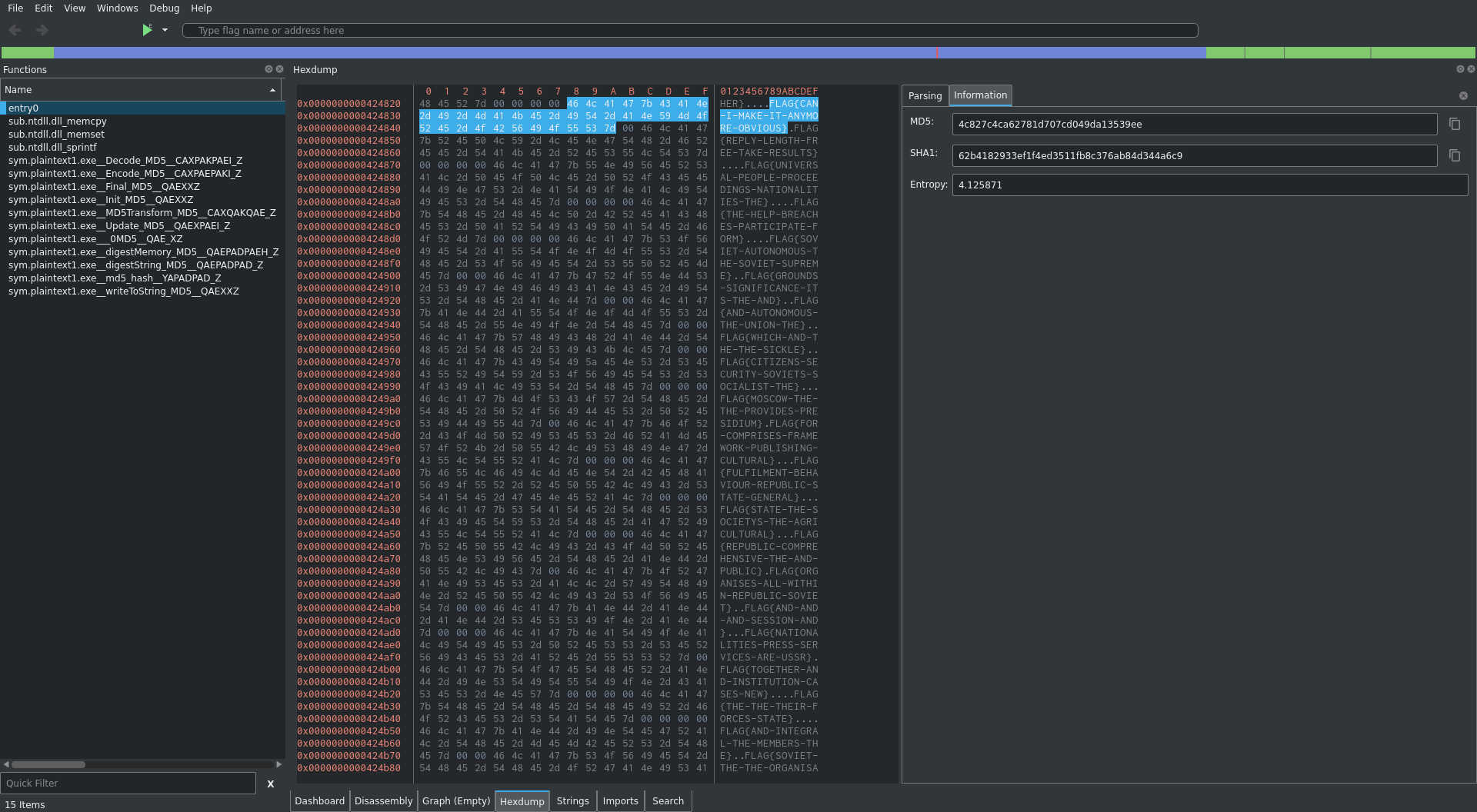
Next a function is called that seems to compute an MD5 hash. On runtime this binary will print the MD5 value of the flag out.
Overall this was a pretty simple challenge, that didnt require really anything more than opening this up in a disassembler. I am still learning to understand assembly code and read it fluently. This first challenge did not require having to read the assembly or really understand it as the flag was pretty apparent off the bat.
More challenge uploads to come!